Dissecting HackTheBox Pro Labs: The Art of Attacking Enterprise Networks

Table of Contents
- Introduction
- Quick Overview of Pro Labs Categories
- Are Pro Labs Designed for Red Team Operators or Penetration Testers?
- P.O.O Mini Pro Labs
- Dante Pro Labs (AKA The Pivot Playground)
- Zephyr Pro Labs (AKA The calm before the storm)
- Offshore Pro Labs (AKA Trust Terror)
- Final Thoughts, Tips and Recommendation
- References
Introduction
HackTheBox Pro Labs have become a defining benchmark in cybersecurity training, offering immersive, real-world simulation environments designed to push the boundaries of ethical hacking skills. These labs are highly valued by cybersecurity professionals for their realism, complexity, and advanced setup with the latest TTPs.
In this blog post, we will dive into the meat and potatoes of 3 major Pro Labs (Dante, Zephyr, Offshore) and POO mini Pro Labs highlighting their core challenges, learning outcomes, and what makes each lab a unique training ground. Whether you’re a seasoned professional or a novice seeking for a challenge, I hope this guide bring some clarity and help you decide which Pro Labs to tackle next.
Quick Overview of Pro Labs Categories
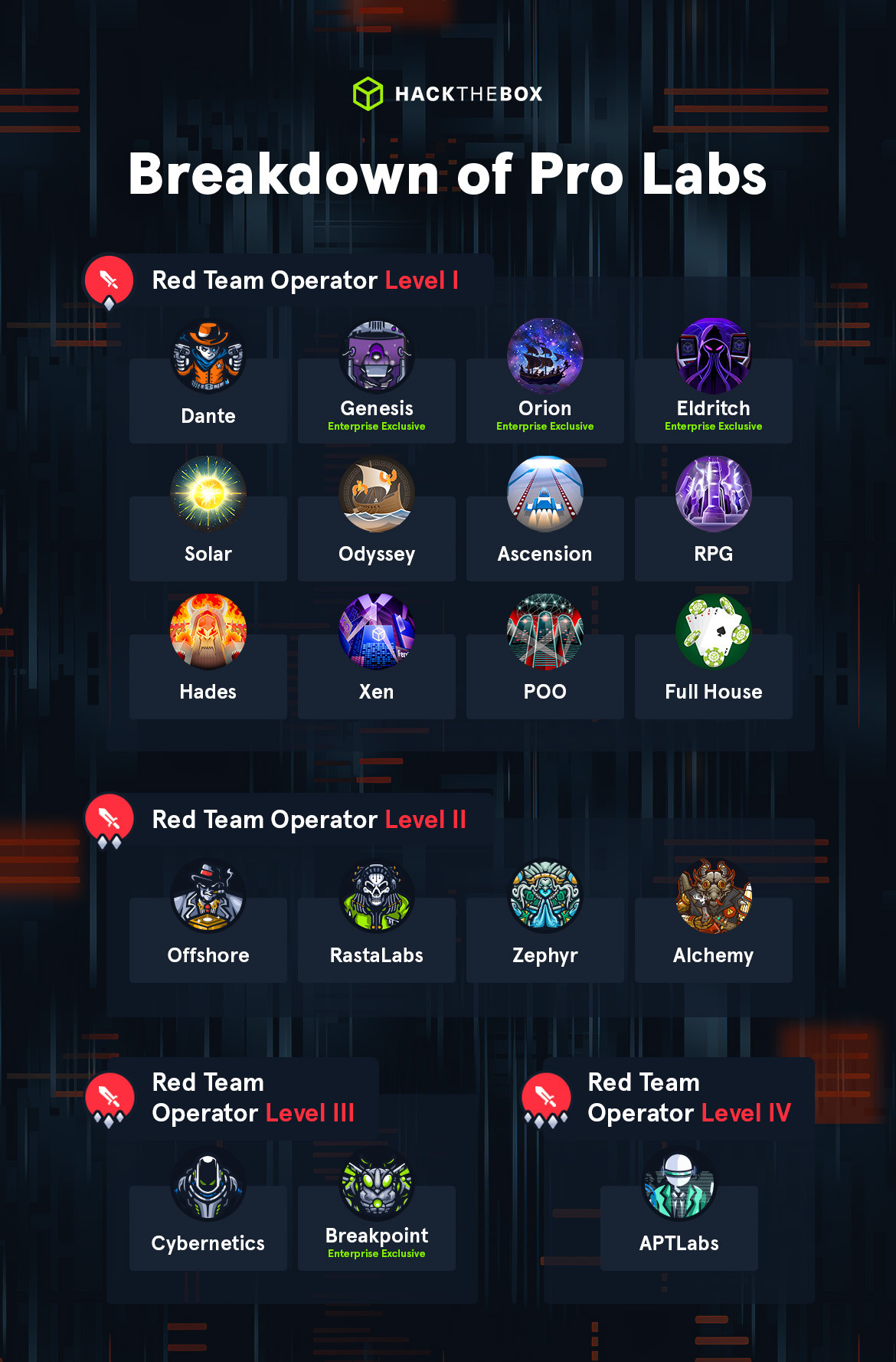
Before dissecting the mentioned Pro Labs individually, it’s essential to have a sneak peek of what they are made of, their purpose, as well as applicability. As you can see below, there are 2 main categories:
- The Primary Bundle: this allows players to gain access to the all Pro Labs shown on the cover image of this post. More details on pricing can be found HERE.
- Enterprise Exclusive:On the other hand comes under a different subscription. I can’t pronounce myself much on this so feel free to explore.
Are Pro Labs Designed for Red Team Operators or Penetration Testers?
At first, I thought HackTheBox Pro Labs were only for Red Team operators but turns out I was wrong. Most labs are Red Team–level, and while shortcuts can work, it’s best to follow the intended approach. Relying on shortcuts or luck might work in these labs at times but may not or rather would never in real engagements. Everything in the lab exists for a reason, so stay observant and take detailed notes.
Despite the name, penetration testers can tackle these labs, hence practice if not learn new skills or techniques. Bear in mind that they are time-consuming, even for seasoned professionals.
This could be due to factors like tools malfunctioning, VPN issues, broken machines, or overlapping attacks. Frustrating moments such as “Why won’t this payload work?” are unavoidable.
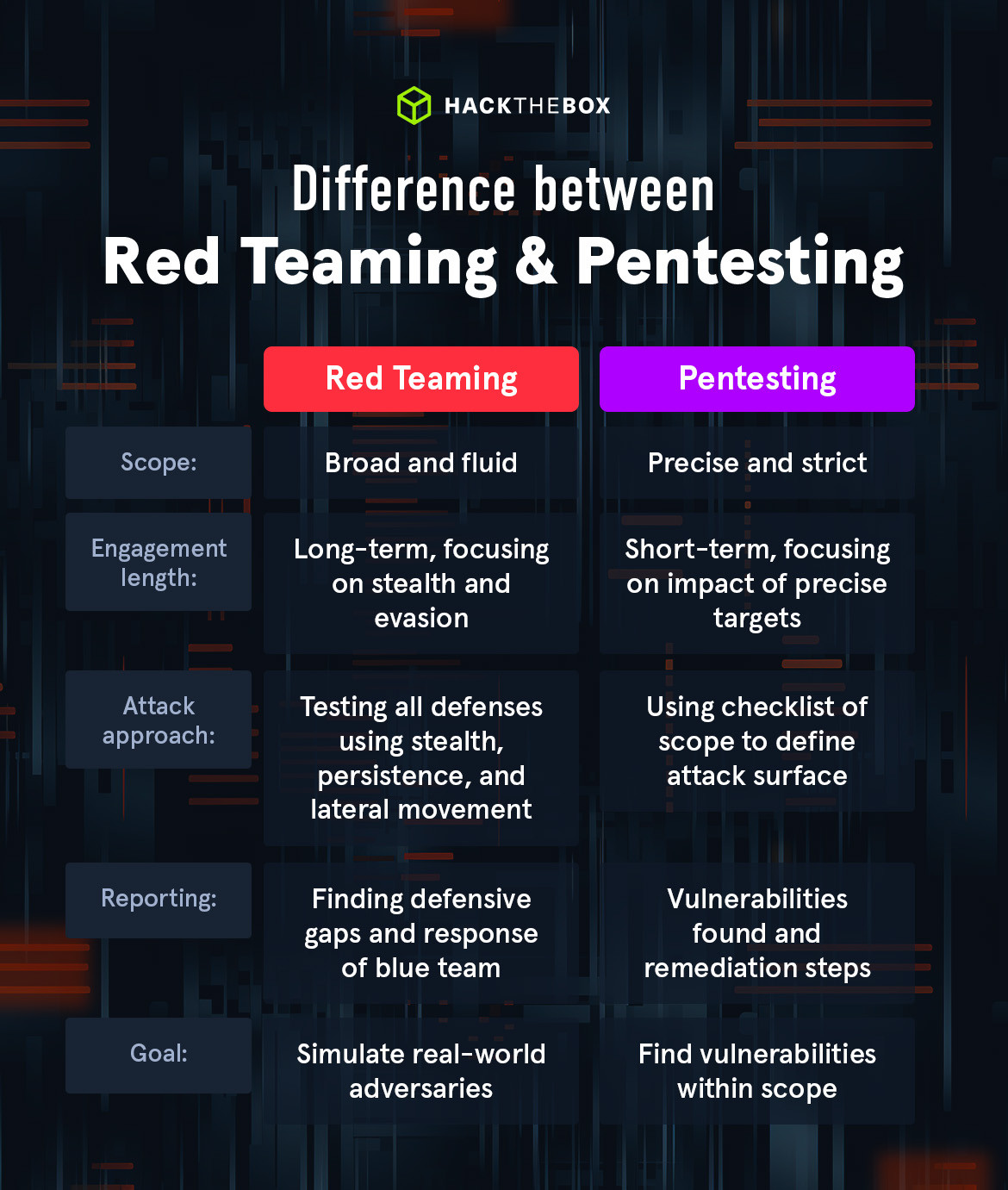
Attached is an HTB blog image highlighting the key differences between Red Teaming and Penetration Testing. Kindly take note if you were unsure or confused about these two terminologies.
With that clarified, let’s dive into the deliverables of these wonderful networks.

Note that the overviews and learning outcomes below are exactly same as described HERE (Check out Lab Scenarios section). However, everything else is my personal opinion and experience with the labs.
As always, I recommend checking other reviews to gain more insights. For obvious reasons, I will try my very best not to throw spoilers, while focusing on the challenges I faced, and a few tips and tricks.
P.O.O Mini Pro Labs
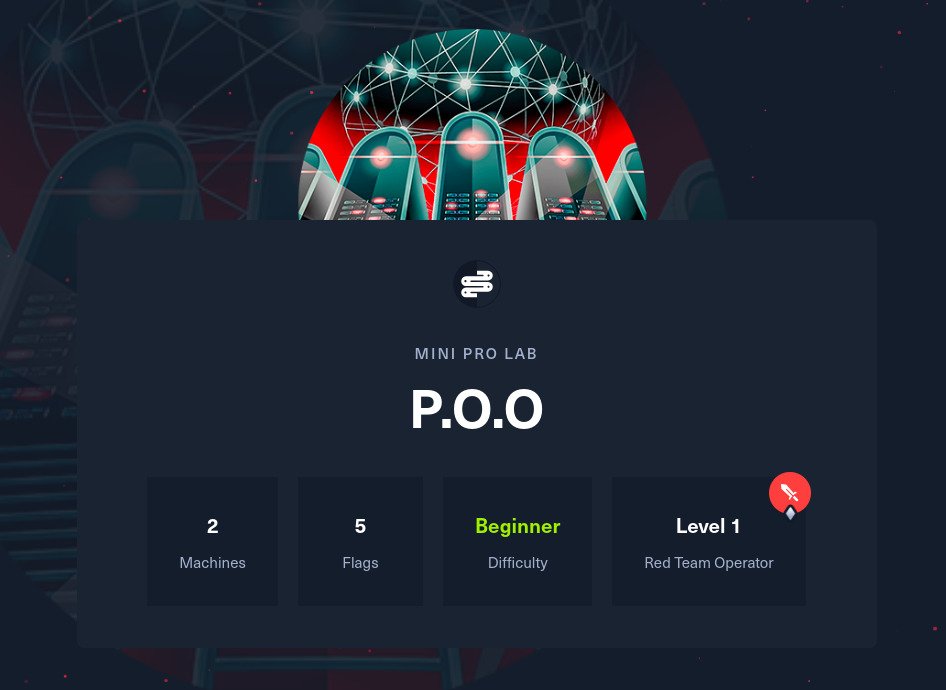
Overview
P.O.O focuses on enumeration, lateral movement, and privilege escalation within small Active Directory environments configured with the latest and greatest operating systems and technologies. The goal is to compromise the perimeter host, escalate privileges and ultimately compromise the domain.
Learning Outcomes
- Enumeration
- Active Directory enumeration and attacks
- Pivoting & Lateral Movement
- Local privilege escalation
- Situational awareness
- Web application enumeration and attacks
Key Takeaways & Insights
- I find it difficult to elaborate on this one without spoiling it to be very honest. However, if you want to get familiar with HTB Enterprise Networks (Pro Labs) at the smaller scale, then this will be a great warm up. Starting with this was instrumental for me, as the roller coaster of emotions and difficulty keeps increasing as I moved forward.
- I found the attacks paths very interesting and I enumerated these machines in ways I never thought I could before. Long story short, it won’t be a waste of time even though you only get 5 flags to capture. Bear in mind that P.O.O is a Pro Lab for a reason and I will let you discover it.
Dante Pro Labs (AKA The Pivot Playground)
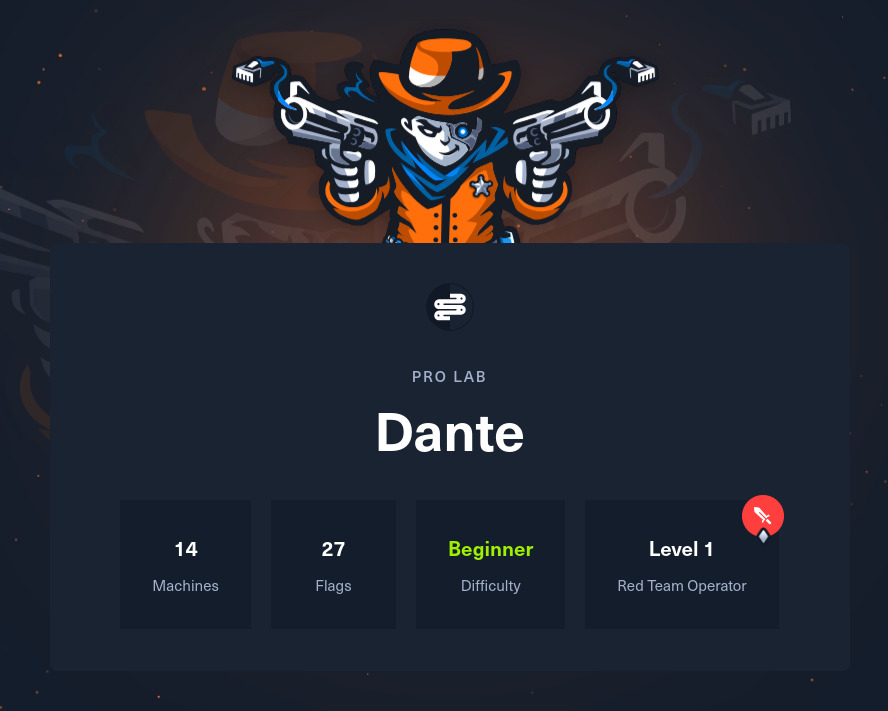
Overview
Dante is a modern, yet beginner-friendly pro lab that provides the opportunity to learn common penetration testing methodologies and gain familiarity with tools included in the Parrot OS Linux distribution.
Learning Outcomes
- Enumeration
- Exploit development
- Pivoting & Lateral Movement
- Local privilege escalation
- Situational awareness
- Web application Attacks
Key Takeaways & Insights
- Dante focuses on network-level penetration testing. Some find it chaotically messy, while others enjoy navigating its pitfalls and can make sense of the chaos.
- PoC and Exploits are all over ExploitDB, GitHub and just a little hint will put you on the right path. Hence, Google is your best ally.
- Ligolo-ng is essential for navigating subnets and pivoting, outperforming tools like ProxyChains, SSH tunnels, or Chisel. Still, sometimes I relied on Chisel for specific hosts.
- A junior penetration tester with strong methodology and patience can tackle Dante, but success depends on experience. While it covers little AD exploitation, it’s excellent for practicing pivoting, understanding enterprise network setups, and sharpening engagement skills.
Zephyr Pro Labs (AKA The calm before the storm)

Overview
Zephyr is an intermediate-level red team simulation environment, designed to be attacked as a means of learning and honing your engagement skills and improving your active directory enumeration and exploitation skills.
Learning Outcomes
- Enumeration
- Evading endpoint protections
- Exploitation of a wide range of real-world Active Directory flaws
- SQL & Relay Attacks
- Lateral movement and crossing trust boundaries
- Privilege escalation
- Web application Attacks
Insights and Reflections
- Several reviews suggest Zephyr to be excellent for CRTP holders and exam prep. I haven’t completed CRTP yet, so I won’t comment directly, but the latest syllabus includes using Sliver C2 on Windows Server 2022, which is invaluable. I didn’t use a C2 for Zephyr, but leveraging one could make handling AV/EDR much easier.
- Besides CRTP, many CPTS veterans note that Zephyr aligns well with the HTB CPTS exam. Dante and Zephyr are often the top two Pro Labs recommended before attempting the CPTS Exam. While Offshore is considered to be an overkill, doing it wouldn’t hurt and will just be icing on the cake.
- While CPTS learning path felt enough, I found the overall experience to be incredibly rewarding allowing me to learn new tricks and TTPs.
Offshore Pro Labs (AKA Trust Terror)

Overview
Offshore is a real-world enterprise environment that features a wide range of modern Active Directory misconfigurations. If you manage to breach the perimeter and gain a foothold, you are tasked to explore the infrastructure and attempt to compromise all Offshore Corp entities.
Learning Outcomes
- Active Directory enumeration and exploitation
- Evading endpoint protections
- Lateral movement
- Local privilege escalation
- Situational awareness
- Tunneling and pivoting
- Web application Enumeration and Attacks
Lessons Shaping the Path Forward
- Firstly, Offshore is time consuming specially for non CRTE, CRTM, or CRTO, CRTL, or even HTB CAPE holders. Don’t get me wrong, you can certainly do it without non of the certs previously mentioned. However, if you decide to go down that path like I did, be ready to be humbled several times, to embrace extreme resilience and composure, and most importantly extensive research every now and then is non negotiable. If you have been through HTB Pro Labs you know the drill.
- BloodHound is essential for mapping the landscape, especially in offshore labs with four forests. Map each domain and forest thoroughly to understand trust relationships and uncover valuable insights.
- A key tip for Offshore is switching VPN instances, it can make unreachable hosts accessible. Many users suggest US over EU instances, partly because some stay broken for days. I’ve been there, it’s frustrating, but you learn as you go.
- Offshore is vast, chaotic, and demanding, but truly rewarding. Cybernetics and RastaLabs (AKA Evasion Madness), however, are tougher and their strict evasion requirements mean msfvenom alone won’t save you without proper obfuscation and evasion techniques.
- If Dante felt messy, this one will blow your mind as FLAGS are everywhere. Thoroughly enumerate every host, and search for strings like “flag”, “OFFSHORE” , or similar. I ran the below command on nearly every host, it saved me, and it might save you too.
powershell.exe -c "Get-ChildItem -Path C:\ -Recurse -Filter *flag*.txt -ErrorAction SilentlyContinue -Force"
Final Thoughts, Tips and Recommendation

- First and foremost, the labs often have many active users, so expect overlapping techniques. For instance, ForceChangePassword is frequently used (thanks to BloodHound) and often by novices, while experienced players take other routes. Artifacts, hashes, or deleted files may also result from others’ actions.
- Establish a solid methodology before starting, or refine one as you progress. CPTS gave me the fundamentals, but success with HTB Labs demands research and resourcefulness. As such, I highly recommend you use Google, the HTB Community, Forum, and Discord.
- Sometimes, it’s best to capture or steal credentials instead of Brute forcing them (Responder, SMBRelay, or OSINT are instrumental). Additionally, credentials reuse is common in the above Pro Labs and it might apply to the rest as well. Hence, familiarity with tools such as NXC or CME can save a lot of TIME.
- Enumeration is key, you may run tools like winPEAS, LinPEAS or living off the land techniques such as built-in powershell commands, for loop, powershell or bash one liners to locate interesting files and attack paths.
- Engage wisely with the community, Discord is your best ally. Check the Pro Labs section for past discussions when stuck, or ask questions to exchange insights with others. Many solutions come from reading, sharing, or helping others, and I remain grateful to those who do the same.
- Take detailed notes and track all findings. Some even practice reporting, which is great. Whatever method or tool you use, never CHARGE IN BLIND. Your motivation to get started is one thing, but perseverance and consistency keeps you going when you’re stuck for days or weeks.
- You don’t need to master C2 frameworks for some Pro Labs, though they shine in Zephyr, RastaLabs, and Cybernetics. For POO and Dante, they’re overkill. Focus on mastering Ligolo-ng for pivots as it’s far more reliable than classics like Proxychains, Chisel, or SSH.
- Be ready to step out of your comfort zone as you will need to use unfamiliar or previously avoided TTPs. HTB Pro Labs are truly time-consuming, with duration varying based on VPN performance, experience in enterprise exploitation, and daily time commitment.
- Lastly, automate wherever possible. Create scripts for repetitive tasks, this saves time and effort. For instance, here’s a bash script I use to add hosts to a Ligolo interface and I keep similar scripts for each subnet in the Pro Labs.
#!/bin/bash
# Interface to use
INTERFACE="ligolo"
# List of target IPs
IPS=(
172.16.x.x
172.16.x.x
172.16.x.x
)
# Loop through each IP and add route
for ip in "${IPS[@]}"; do
echo "Adding route to $ip via $INTERFACE..."
sudo ip route add "$ip" dev "$INTERFACE"
done
echo "All routes added successfully."Referencess
- The Hacker Recipes
- Hacktricks — Wiki
- AD Exploitation Cheat Sheet | GitHub
- Pre-Compiled Binaries | GitHub
- AD PenTesting Tools | GitHub
- Awesome AD PenTest Tools | GitHub
- Toolies | GitHub
- Introduction to Enterprise Level Attack Scenario | HTB Blog
- HackTheBox Pro Labs | Overview & Learning Outcome
- HTB Labs Subscription | HTB Article
- OSEP Tools | GitHub
- HTB Pro Labs - Deep Dive | LinkedIn Blog